
Author: Karim Zaki
• MBA Major MIS
• MCP (Microsoft Certified Professional) Windows XP.
• Microsoft Certified in (Managing and Maintaining Microsoft server 2003).
• Microsoft Certified in (implementing, Managing, and maintaining a Microsoft windows server 2003 infrastructure)
• Microsoft Certified in (Maintaining a MS Win Server 2003 Active Directory)
• MCSA 2003
• ISA 2006 Microsoft Internet Security and Acceleration Server 2006, Configuring
• MCTS Microsoft Certified Technology specialist
• MCITP 2008 (Microsoft Certified IT professional)
• MCSA 2012 Server (Microsoft Certified solution Associate)
• AZURE Administrator Associate (AZ-103)
• MS 365 Identities and services (MS-100)
• MS 365 Mobility and security (MS-101)
• Microsoft 365 Certified: Security Administrator Associate (MS-203)
• Microsoft 365 certified enterprise administrator expert (MS-500)
• Messaging Administrator Associate (MS-203)
• Azure Security Engineer Associate (AZ-500)
• Information Security: Context and Introduction
• Microsoft Security Operations Analyst

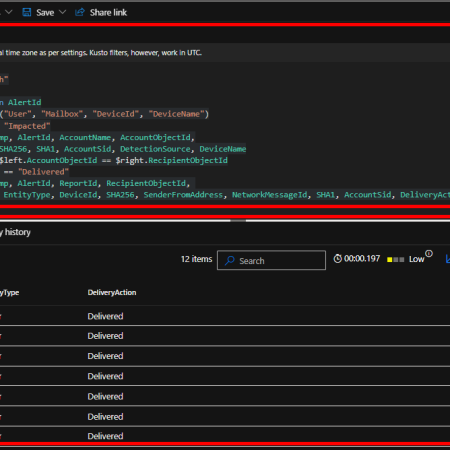
Custom detections rules
Penetration test and assessment

How to recover data from a failed Exchange Server Database Availability Group using Stellar Repair for Exchange

Windows Hello in hybrid environments using Cloud Kerberos trust policy.
